ZERO2INFYNITE also provide NETWORK-VULNERABILITY ASSESSMENT AND PENETRATION SERVICES to different organisation. Vulnerability Assessment in any system can be defined as Systematic and methodical evaluation of exposure of assets to attackers, forces of nature, and any other entity that could cause potential harm and to correct those vulnerability is doing penetration testing. Zero2infynite has gained great exposure in the field of network va-pt.
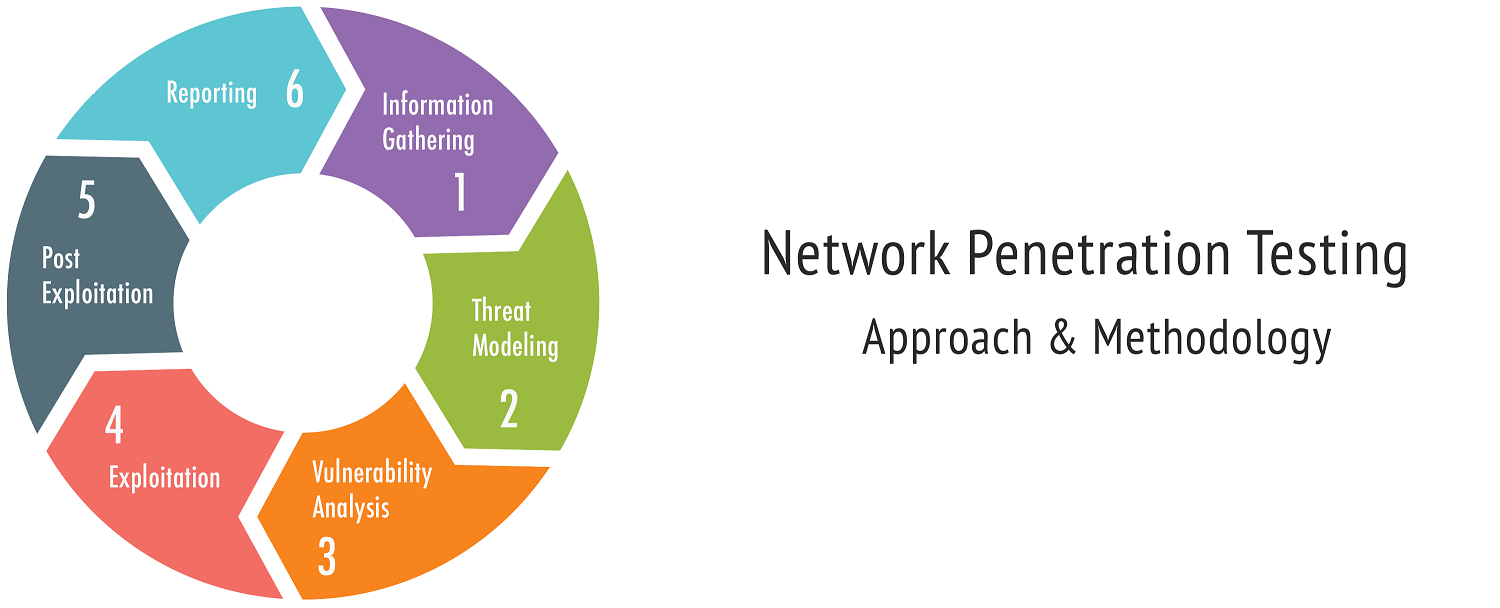
Our Approach For Network VA/PT
STAGE 1: PLANNING AND INFORMATION GATHERING
- Share the assessment methodology documents with the client.
- Ask for details of the web applications in scope for the assessment.
- scope to decide potential impact of scanning activities.
- Share contact details of Team Leads and Project Manager from company.
STAGE 2:
- A: WHITE BOX TESTING
- B: BLACK BOX TESTING
- C.GREY BOX TESTING
STAGE 3:
REPORTING AND KNOWLEDGE TRANSFER
- Conduct a knowledge transfer exercise to the technical team
- Present the findings to the technical and management teams
- Hand over final set of deliverable s to the client
Tools for network-VAPT
1. NMAP
- Nmap (“Network Mapper)utility for network discovery and security auditing. It is useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime
- Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering,
2. Nessus
- Nessus scan your personal home network (up to 16 IP addresses per scanner) with the same high-speed, in-depth assessments and agentless scanning convenience.
3. GFI LanGuard
- GFI LanGuard provides a detailed analysis of the state of your network. This includes applications or default configurations posing a security risk.
4.SPARTA
- SPARTA is a python GUI application which simplifies network infrastructure penetration testing by aiding the penetration tester in the scanning and enumeration phase.
5. Metasploit
- The Metasploit Framework contains a suite of tools that you can use to test security vulnerabilities, enumerate networks, execute attacks, and evade detection. At its core, the Metasploit Framework is a collection of commonly used tools that provide a complete environment for penetration testing and exploit development.
6. DMitry
- (Deepmagic Information Gathering Tool) is a UNIX/(GNU)Linux Command Line Application coded in C. DMitry has the ability to gather as much information as possible about a host. Base functionality is able to gather possible subdomains, email addresses, uptime information, tcp port scan, whois lookups, and more
7. Nikto
- It checks for server configuration items such as the presence of multiple index files, HTTP server options, and will attempt to identify installed web servers and software. Scan items and plugins are frequently updated and can be automatically updated.
8. Wireshark
- Wireshark is very similar to tcpdump, but has a graphical front-end, plus some integrated sorting and filtering options.
summery
Zero2infynite ultimate goal is to provide effective satisfaction to the client in order to find all vulnerabilities at client place and removing them at the same time.
We are finalizing the After the successful penetration into the system, privilege escalation technique is used to identify and escalate access to gain higher privileges, such as registry/root access or administrative privileges to that particular it environment system or network.finally binding it with documents , reports and the effort made.