WEB APPLICATION VA/PT SERVICES -(VULNERABILITY ASSESSMENT AND PENETRATION TESTING)
ZERO2INFYNITE provides effective service in web application -vulnerability assessment and penetration testing domain.Customer satisfaction and quality service is our ultimate goal, Zero2infynite focuses on problem solving methodology and believe in giving efficient service to our customer.
Our purpose is to to utilize active exploitation techniques in order to evaluate the security of the application against best practice criteria and to validate its security mechanisms and identify application level vulnerabilities.
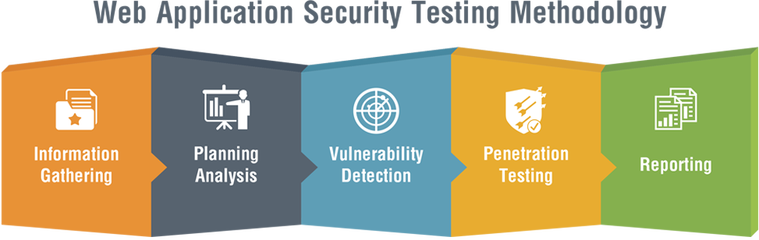
OUR APPROACH FOR WEB APPLICATION VULNERABILITY ASSESSMENT AND PENETRATION TESTING
STAGE 1: PLANNING AND INFORMATION GATHERING
• scope to decide potential impact of scanning activities.
• Get the contact details of stake holders that need to be kept posted of the scanning activities.
• Share contact details of Team Leads and Project Manager from company.
STAGE 2:
A: WHITE BOX TESTING
B: BLACK BOX TESTING
C. GREY BOX TESTING
STAGE 3: APPLICATION SECURITY ASSESSMENT
• Assess the security of the selected applications, focusing on remotely exploitable vulnerabilities, application security architecture, design and implementation.
• Assess the controls with respect to user access, privilege levels, development and delivery, and overall design of the applications
STAGE 4: REPORTING AND KNOWLEDGE TRANSFER
• Submit the final and detailed set of reports with in-depth information to fix the vulnerabilities and an efficient and effective follow-up plan
• Conduct a knowledge transfer exercise to the technical team
• Present the findings to the technical and management teams
• Hand over final set of deliverables to the client
TOOLS GOING TO USE IN WEB APPLICATION VAPT
Nessus
- Nessus scan your personal home network (up to 16 IP addresses per scanner) with the same high-speed, in-depth assessments and agentless scanning convenience.
Open VAS
- OpenVAS is a framework of several services and tools offering a comprehensive and powerful vulnerability scanning and vulnerability management solution.
Vega
- Vega can help you find and validate SQL Injection, Cross-Site Scripting (XSS), inadvertently disclosed sensitive information, and other vulnerabilities. It is written in Java, GUI based, and runs on Linux, OS X, and Windows.
DirBuster
- DirBuster searches for hidden pages and directories on a web server. Sometimes developers will leave a page accessible, but unlinked; DirBuster is meant to find these potential vulnerabilities. This is a Java application developed by OWASP.
sqlmap
- sqlmap is an testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
NMAP
- Nmap (“Network Mapper)utility for network discovery and security auditing. It is useful TOOL for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
- Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering,
Nikto
- Nikto is an web server scanner which performs comprehensive tests against web servers for multiple items, including over 6700 potentially dangerous files/programs, checks for outdated versions of over 1250 servers, and version specific problems on over 270 servers.
Burp
- Burp Suite is an integrated platform for attacking web applications.
Amap
- Amap is a next-generation tool for assisting network penetration testing. It performs fast and reliable application protocol detection; independently of the TCP/UDP port they are being bound to.
summery
Zero2infynite will be performing web- penetration testing effectively at client place and giving complete satisfaction from the vulnerabilities.
We are finalizing the After the successful penetration into the system, privilege escalation technique is used to identify and escalate access to gain higher privileges, such as registry/root access or administrative privileges to that particular its environment system or network.Finally binding it up with reports and documentation.